ZipXPS provides multiple powerful methods to help you recover the lost password of an encrypted file in your Zip archive or restore the content of the file itself. This page will elaborate on these methods.
Exhaustive Search
Exhaustive Search [1] is a generic approach to unlock your encrypted Zip file: You provide a list of words to ZipXPS and ZipXPS tries these words one after another until one matches the password of your Zip file or all words from the list are exhausted.
The main benefit of this technique is that you do not need to find a weakness in the underlying encryption algorithm or its implementation for the recovery process to succeed. Additionally, exhaustive search is – at least in principle – able to recover your Zip password in any case. This is due to the trivial fact that finding a Zip password by brute force is equivalent to that Zip password being on the given list of words. Hence, if your list of words is just large enough, you will definitely recover your Zip password. Of course, the downside is, that depending on the number of words on your list (which is implied by the supposed length and complexity of your Zip password) and the speed of the password verification process (which depends on the complexity of the encryption algorithm), it might take an infeasibly long time to find a matching Zip password on your list.
Currently, ZipXPS offers you two flavors of brute-force Zip password recovery. These differ in the type of source of your list of words: either one or more dictionary files or one or more so called charset masks.
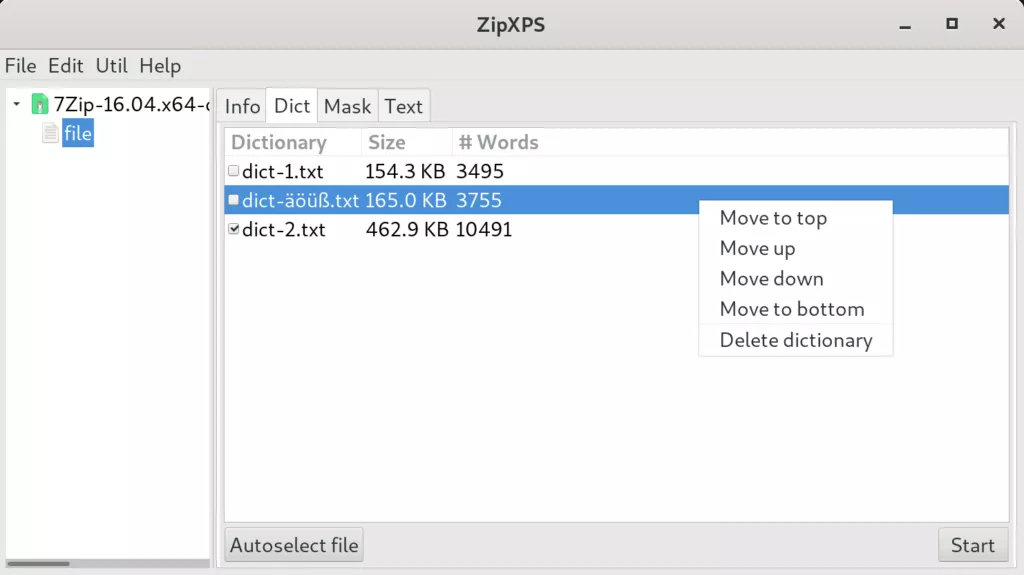
Dictionary Method
With the dictionary-based Zip password recovery method, in short the dictionary method, the list of words you supply to ZipXPS is built from one or more dictionary files, also simply called dictionaries. ZipXPS then works through these dictionaries – in parallel on a multi-core computer – and checks for each word from each dictionary whether that word is a matching Zip password for the selected file from your Zip archive or not. ZipXPS will do so until a match is found or all dictionaries are processed.
The dictionary files in ZipXPS are simple text files with one potential Zip password per line. This user-friendly input format makes unlocking your encrypted Zip archive with the dictionary-based Zip password recovery method straightforward.
Mask Method
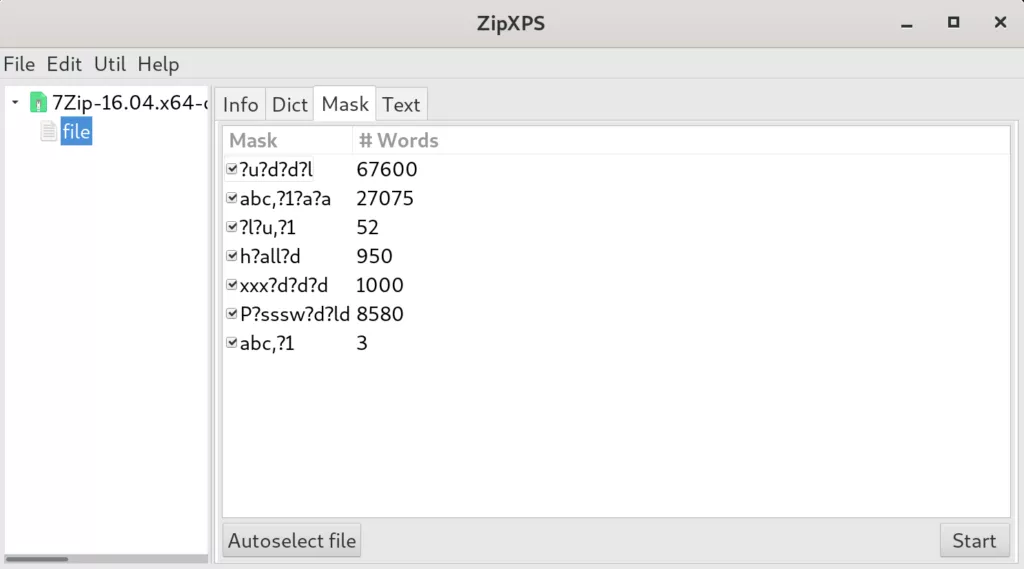
If your memory of the original password of an encrypted file in your Zip archive is somewhat blurry, you might want to define the list of password candidates for the search process as a so called charset mask. A charset mask is a very compact yet powerful specification of a set of words. With a charset mask you provide a set of characters, i. e., a charset, for each position in your potential Zip password. Then the product of these charsets generates the set of password candidates. Some charsets are already predefined for you. These are identified by a short mnemonic for ease of use. For instance, the charset mask
Zip?d?d?d
contains three times the predefined charset ?d which denotes the digits 0, 1, …, 9. The entire charset mask thus represents the set given by the words Zip000, Zip001, …, Zip999.
ZipXPS implements the charset masks as used by the popular open-source software Hashcat with a few minor extensions. In particular, the following charsets are predefined in ZipXPS:
- ?d – digits 0, 1, …, 9
- ?l – lowercase letters a, b, …, z
- ?u – uppercase letters A, B, …, Z
- ?s – ASCII special characters &, %, ., *, …
- ?a – all printable ASCII characters
- ?b – all octets 0x00, 0x01, …, 0xff
Don’t be scared though. The ZipXPS user manual supplied with ZipXPS describes the format and usage of charset masks comprehensively.
Known-Plaintext Method
Besides exhaustive search, ZipXPS also implements a cryptoanalytical approach for password and data recovery. That approach – originally described by Eli Biham and Paul Kocher in “A Known-Plaintext Attack on the PKZIP Stream Cipher” – exploits well-known, scientifically published design flaws in the traditional Zip encryption algorithm (PKZIP Encryption, also named ZipCrypto in 7-Zip). It requires you to supply a few known bytes from the original, unencrypted representation of a PKZIP-encrypted file in your Zip archive. Under those circumstances, ZipXPS will enable you to recover the full content of that file and any other file in the same or another Zip archive that was PKZIP-encrypted with the same password. The password itself can often also be restored. If the specific requirements of this method are met, it will succeed very quickly.
The ZipXPS user manual distributed with ZipXPS contains all the information you need to successfully employ this sophisticated recovery method.
References
- Biham, E., Kocher, P.: A Known Plaintext Attack on the PKZIP Stream Cipher. In: Preneel, B. (ed.) FSE 1994. LNCS, vol. 1008, pp. 144-153. Springer, Heidelberg (1995)
[1] also known as brute-force method